I'd ignore step 4 and stick to hashtags only... from there you'll end up finding interesting people anyway.
I thought session had been replaced with simplex.
following hashtags
That's the advice i usually give: hashtags, not people... interesting people will follow.
...but Pleroma!...
the “Department of Government Efficiency”
...the DoGE?...
I’d rarely get scam calls or texts before I switched but since I’ve been with o2, I get 5-10 calls a week.
Maybe O2 should stop selling your data?
Someone's been tampering with skynet...
Install the headless version, no GUI:
${EDITOR} /etc/apt/apt.conf.d/99noRecommends
APT::Install-Recommends "0";
APT::Install-Suggests "0";
and then run apt update.
Then install fluxbox session manager, oughta be enough.
they have paid developers
They should pay lawyers as well.
And ofc this depends on new trees being planted in its stead.
Hence farming trees...
With Headscale being an open source, self-hosted implementation of the Tailscale control server.
Screw communities, i just wanna influence everywhere... great.
Apparently so... couldn't be bothered with an account to go check...
...soon to be replaced by coal once Trump steps in...
Can't find freetube on fdroid so no.
Tailscale
Have you considered Headscale?
Mr Wallace will make you regret that.
due to deployment hell you end up using docker
Maybe tackle that deployment hell instead of band-aiding it with docker?
The comment section mentions that conundrum as well... quite interesting.
The comment thread in that article is interesting. Grep for Ada.
Eighteen years of ABI stability in curl
> Exactly eighteen years ago today, on October 30 2006, we shipped curl 7.16.0 that among a whole slew of new features and set of bugfixes bumped the libcurl SONAME number from 3 to 4.
The German police have successfully deanonymized at least four Tor users. It appears they watch known Tor relays and known suspects, and use timing analysis to figure out who is using what relay. T…

> The German police have successfully deanonymized at least four Tor users. It appears they watch known Tor relays and known suspects, and use timing analysis to figure out who is using what relay. > Tor has written about this. > Hacker News thread.
China has a space station — it’s called Tiangong, the first module was launched in 2021, and it’s all going quite swimmingly, thank you very much. That’s essentially what we…

Probably not too many people around the world celebrated November 1st, 2023, but on this momentous date FreeBSD celebrated its 30th birthday. As the first original fork of the first complete and op…

Probably not too many people around the world celebrated November 1st, 2023, but on this momentous date FreeBSD celebrated its 30th birthday. As the first original fork of the first complete and op…

When it comes to comedy, there is a principle that a physical gag will be funny if done 3 times, but then will stop being funny on any further attempts unless it reaches a much higher number, like …

Maybe the CEO should've asked for advice here.
After federal police came to an employee’s house to ask questions, encrypted messaging company Session has decided to leave Australia and switch to a foundation model based in Switzerland.

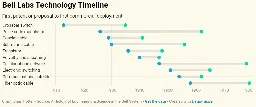
It’s been said that the best way to stifle creativity by researchers is to demand that they produce immediately marketable technologies and products. This is also effectively the story of Bel…
So they were from Sudan...
Vice President Kamala Harris is now calling for a regulatory framework that would “protect” American crypto holders.

Vice President Kamala Harris is now calling for a regulatory framework that would “protect” American crypto holders.

As a last-ditch effort, James Howells is bringing his disagreement with Newport council over his lost Bitcoin fortune to court in Wales.

We’ve all heard stories of the dangers of 3D printing, with fires from runaway hot ends or dodgy heated build plates being the main hazards. But what about the particulates? Can they actually…

For the first time, NASA has used lasers to send data from deep space to Earth — and the data for the historic demonstration was a cat video.

Finally, the singularity has happened.
Terminology question
Greetings, non-native and curious here.
I know a transport manifest is the document that lists contents being transported: items, quantities, etc... often used in long-haul trucks.
Are there other documents like this? Invoiceable? If i own a small business and go buy, say, a laptop at another business (requiring such a document since it's a B2B transaction and the item will be carried in a company vehicle), is it still a "transport manifest" or does it have another name?
Best places to buy batteries?
I'm looking to replace the battery of a ThinkPad T410 (and maybe of a T480 as well but i haven't tested them yet).
What are the recommended places to get them in the EU?
I've already found ifixit for the T480 but i'm more focused on the T410 atm.
Researchers posted AI-generated nude images to Twitter to see how the company responds to reports of copyright violation versus reports of nonconsensual nudity.

> Twitter will remove nonconsensual nude images within hours as long as that media is reported for having violated someone’s copyright. If the same content is reported just as nonconsensual intimate media, Twitter will not remove it within weeks, and might never remove it at all, according to a pre-print study from researchers at the University of Michigan.
The U.S. government now appears free to sell 69,370 Bitcoin that it seized from a Silk Road-affiliated wallet.

> The U.S. government now appears free to sell 69,370 Bitcoin that it seized from a Silk Road-affiliated wallet.
The definitive roadmap for your self-hosting journey
> Key Takeaways > Start with Type-2 hypervisors for an easy beginning. > Explore personal cloud platforms for and venture into Docker containers. > Check out Proxmox when you want to build a home lab specializing in self-hosting services.

