How is the situation of nix/nix-darwin/home-manager on macOS?
Used nix last year but dropped it after home-manager decided to unlink the apps from the Applications directory.
How is the current situation on usability of nix-Darwin + home-manager + brew?
Packages still fails to get indexed correctly in spotlight? I really like a fully repro environment but the fact that the usu ability was low bothered me a lot.
A raspberry with Adguard + unbound, a zimaboard with truenas scale running the -arr suite, nextcloud, homeassistan, homarr, headscale and caddy 2x2TB nvme and 3x 4tb HDD I recently got a new PC and I think I will convert it to being part of the homelab, it has a ryzen 7 3xxx and a 2070 super.
Ye you are right but I was talking of 3D enclosures where you can put a zimaboard or whatever mini pc.
The difference is that you need way more interaction. Expose a webserver on the internet and check how many requests you get from just bots.
You can control what you navigate and how to interact with the outside world, but you can’t control how the outside world will interact with your services.
Don’t expose anything from your local network to the internet (unless you want multiple new sysadmins in your house). Try tailscale instead.
Anyone knows if there is any project for a modular NAS? Have been looked into it for a while but without success
It's pretty funny, because from mechanicalkeyboards they suggested to post here because you have more knowledge on low profile keyboards.
Do anyone have feedback on this?
https://chosfox.com/products/chosfox-l75-keyboard-kit?variant=42798174732482
Looks promising
Row staggered but not splitted.
How much like the corne do you want it to be?
like a normal keyboard and not split
Also, how DIY do you want to get?
As long as no soldering is required I am up for everything
Low profile keyboard compatible with choc switches
I am looking for a low profile keyboard compatible with the choc switches. I plan to put the choc sunset on it. I was looking for something similar to the Corne, just without the ergo-split thing. A standard 65-75% would work.
Bonus for hot swappable and no soldering required.
WannaCry targeted hospitals, businesses and similar machines.
WannaCry targeted everything with SMB exposed, blindly.
Also, you should read more about security through obscurity, the fact that "no one will target you because you are a low-value target" is a false sense of security.
I don't know why the author of the video didn't mention it but LockDown mode is really useful.
At least for me the default is lockdown mode on and appropriate exceptions for websites I trust.
I believe the risk of running outdated software is super inflated and mediatic, 99% of people would be absolutely fine running a version of Android from 3 years ago or Windows 8.
That's the same thing people running windows XP on internet were thinking in 2017.
Then WannaCry arrived and they got their data encrypted :)
Perhaps images, video, font etc. rendering could be compromised?
Yes, it already happen in the past. Also the Wi-Fi and Bluetooth stack got exploited, like multiple kernel drivers.
But it shouldn't be a matter of "in the past was X exploited?" but more on having a correct security posture.
Honestly if you are arguing about wasting a "perfectly working phone" you should blame it on the vendor, especially Android devices vendors have this let's say "defect" of dropping the support after 4/5 years.
Also not going to talk about custom ROMs (with the super rare exclusion of some) managed by god knows who, without any security team behind.
Since even the NFC and Cellular Network stack got vulnerabilities the only way you would consider an old phone "safe" to use is just turning it into the equivalent of a local ARM server.
Also pretty fun seeing the replies in the original post talking about how Google Play store shouldn't have malware on it.
Low profile keyboard compatible with choc switches
I am looking for a low profile keyboard compatible with the choc switches. I plan to put the choc sunset on it. I was looking for something similar to the Corne, just without the ergo-split thing. A standard 65-75% would work.
Do anyone knows if it support local-only without joining the p2p network?
Exploited in the wild, reported in April, no fix since then?
Edit: looks like it was fixed on the 26th of April, why is tagged as 0day?
Ahaha I had this exact same experience. Locked out because bitwarden didn’t get the code correctly. “Luckily” the jwt token never expires so I was able to log back in without the 2FA.
You think that being convicted for lifetime is a solution anyway?
Honestly curious, why? I live in a country that doesn’t have it but I don’t see downsides if the crimes committed are way too bad. For example, why keeping alive (with contributors money) a serial killer?
So in the end you got removed.. I honestly have no idea how they want to do an IPO like that
I wonder if people when talking about AI just ignore the fact that it’s software and has the same issues and vulnerabilities related to that.. recently I see a lot of posts talking about “AI security” and in the end are stuff known since 1995…
Manjaro 0day LPE via pamac
Manjaro LPE. Contribute to c-skills/vala-vala-hey development by creating an account on GitHub.
Set default language to English
What about setting the new language of a post to English? There are people that don’t know how lemmy works that keep on opening new posts and leaving the language to “Undetermined” by mistake so no one can answer them.
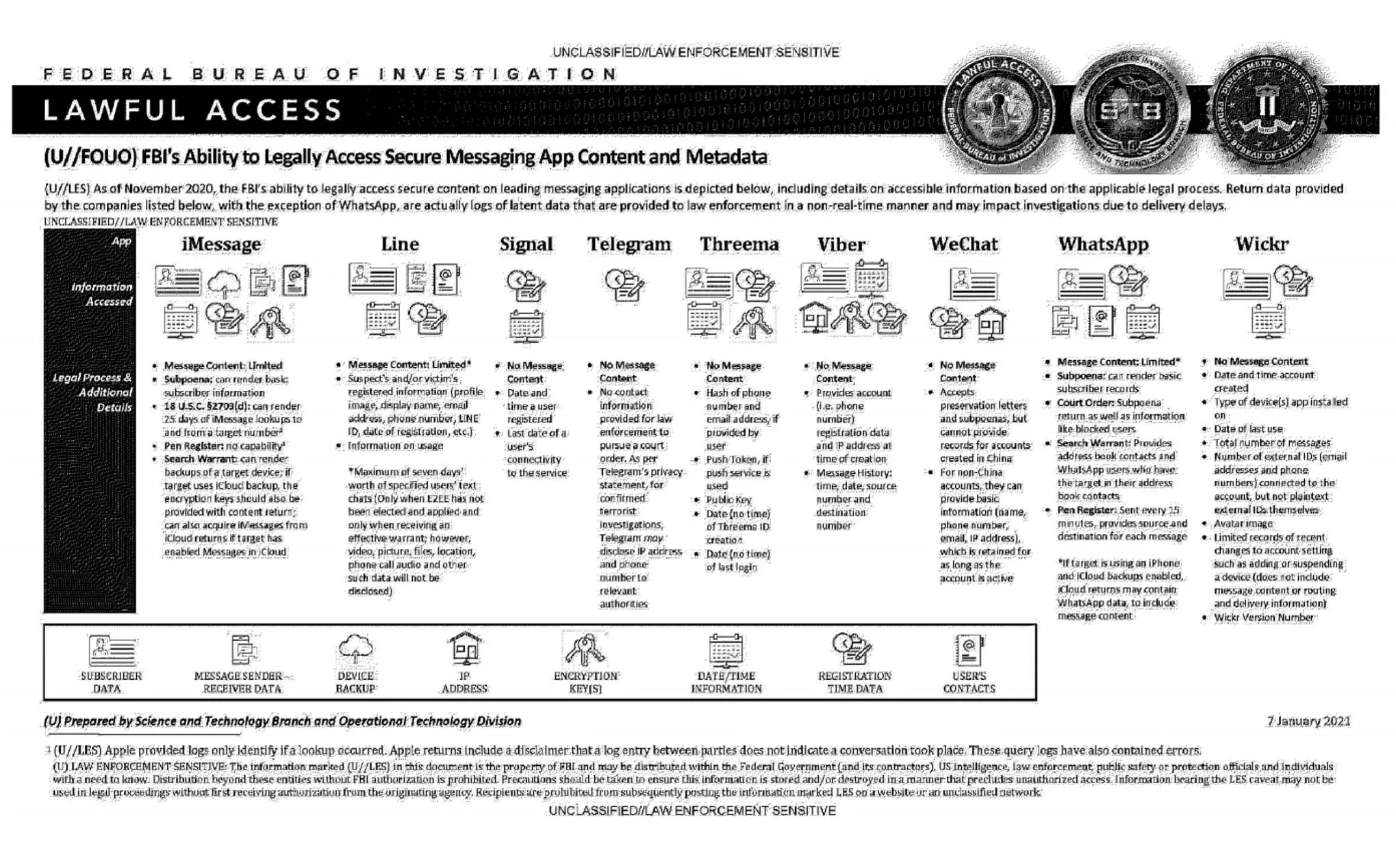
Unclassified FBI Document: Ability to legally access Secure Messaging App Content and Metadata (January 2021)

cross-posted from: https://beehaw.org/post/789646
> An official FBI document dated January 2021, obtained by the American association "Property of People" through the Freedom of Information Act. > > > This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata ("Pen Register") or connection data retention law ("18 USC§2703"). Here, in essence, is the information the FBI says it can retrieve: > > * Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone. > > * Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location). > > * Signal: date and time of account creation and date of last connection. > > * Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing. > > * Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date. > > * Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination). > > * WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users. > > * WhatsApp: the targeted person's basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time ("Pen Register"); message content can be retrieved via iCloud backups. > > * Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting. > > TL;DR Signal is the messaging system that provides the least information to investigators.
Unclassified FBI Document: Ability to legally access Secure Messaging App Content and Metadata (January 2021)


cross-posted from: https://beehaw.org/post/789646
> An official FBI document dated January 2021, obtained by the American association "Property of People" through the Freedom of Information Act. > > > This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata ("Pen Register") or connection data retention law ("18 USC§2703"). Here, in essence, is the information the FBI says it can retrieve: > > * Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone. > > * Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location). > > * Signal: date and time of account creation and date of last connection. > > * Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing. > > * Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date. > > * Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination). > > * WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users. > > * WhatsApp: the targeted person's basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time ("Pen Register"); message content can be retrieved via iCloud backups. > > * Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting. > > TL;DR Signal is the messaging system that provides the least information to investigators.